In the age of digitalization and online consumerism, it is getting increasingly important to provide safe and secure online retail experiences.
In the digital era, web applications are susceptible to cyber-attacks, web security risks and data leakage at all times.
Cybercrime is at an all-time high, and it is estimated to cost companies an astonishing amount of $10.5 trillion annually by 2025.
Here are the types of apps that are at the risk of sensitive data leakage:
What is data leakage?
Data leakage is an unauthorized transmission of sensitive or confidential data used for malicious purposes by hackers.
An insecure app can lead to a loss of credibility and brand loyalty for a company as the consumer can no longer trust the company’s app to make a purchase or any kind of transaction.
It is crucial for companies and developers to be aware of the security risks to successfully prevent cybercrime and deliver safe user experiences.
This is where OWASP Top 10 comes into play!
Let’s start by discussing what is OWASP…
What is OWASP?
Founded in 2001 by Mark Curphey, OWASP is a non-profit international organization dedicated to improving the security of web application software all over the world.
What does OWASP stand for?
Open Web Application Security Project
OWASP meaning is simple: Through numerous open-source projects, thousands of community members and educational training conferences, the OWASP organization is the main source of software security for developers.
They offer a plethora of software security materials like videos, tools, forums and documentation, and all of their content is freely available for everyone on OWASP’s website.
The best content that they’ve released as of yet is the OWASP top 10 for tackling software and mobile vulnerability from issues like data leakage and cyber-attacks.
Now you may be wondering what is OWASP top 10, let’s clarify.
What is OWASP Top 10?
The OWASP Top 10 represents a list of the most threatening security risks to web applications and web development, and the list is updated and optimized every few years. It is a standard report for spreading awareness among developers and technologists.
This ranked list is created by security experts around the world, and the web security risks are ranked according to the frequency of the vulnerabilities, the impact of the security risk and the severity of the security flaws.
Its main objective is to help developers produce a better and more secure codebase for companies, minimizing security risks and building a robust software development culture.
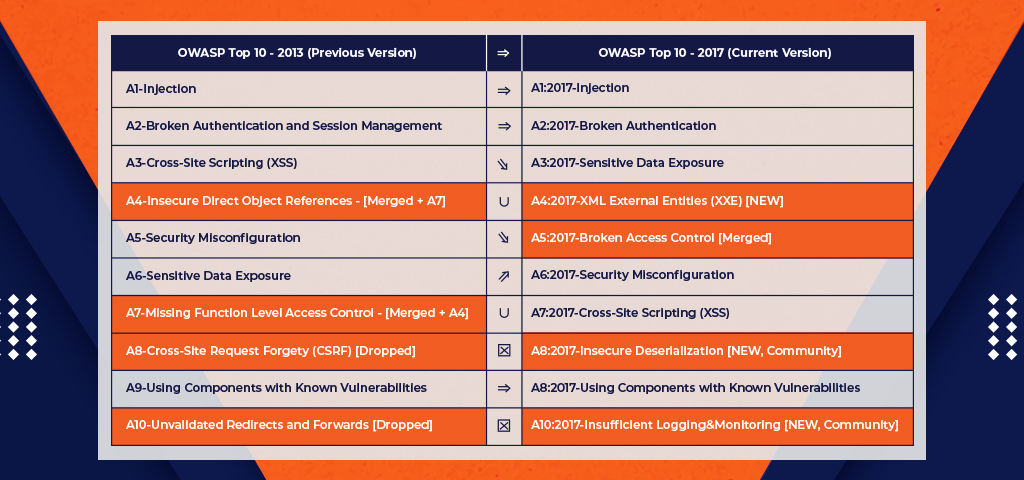
Here’s a list of the OWASP top 10 of 2013 compared to the updated OWASP top 10 of 2017:
Without further ado, let’s discuss each of the latest OWASP Top 10 in detail.
Injection
Broken Authentication
Sensitive Data Exposure
XML External Entities (XXE)
Broken Access Control
Security Misconfiguration
Cross-Site Scripting
Insecure Deserialization
Using Components With Known Vulnerabilities
Insufficient Logging & Monitoring
1. Injection
All the data in a website or web application is stored in databases in form of queries, which is written in a Structure Query Language (SQL) most often than not. Web application retrieves, adds, removes and modifies data through SQL, like when a consumer fills up a questionnaire with personal information and data.
The users’ sensitive data in the questionnaire can be easily hacked for malicious intent by changing the web application’s code specifically for the SQL query.
With this insecure cryptography, a hacker can gain access, steal, view, delete and tamper confidential data for personal gain.This web app vulnerability is the result of insufficient authentication of user information, allowing intruders to input special requests that deceive the web application.
The best way to avoid this OWASP top ten security risk is by separating the database from the queries and commands, which means segregating them from the web app logic.
This can be done in multiple ways:
- Remove the use of parameterized queries and interpreters by using a safe & secure API
- Add a whitelist (server-side input authentication)
- Use the escape syntax in the interpreter to avoid special characters in the web application
- Minimize data exposure in case of an SQL injection by using database controls like LIMIT SQL within the queries
2. Broken Authentication
This is one of the most critical security risks in the list of OWASP top 10. Whenever a web application needs to distinguish and identify users, it uses session cookies. After the login is authenticated via username and password, a specific identifying cookie is saved in storage. This is the process of user identification and recognition of a web application.
If the web application’s IT architecture does not implement additional verification of the user’s IP address or multiple access in a single session, a hacker can gain access to the identifier and the web application via the user’s account.
If it’s a bank account or a web application that contains payment gateways, the consequence of this security breach and unverified access can adversely affect the original user.
This OWASP top ten security risk can be avoided by:
- Implement password optimization by checking the strength of the password used by a user
- Implement multi-factor authentication for double-checking login information
- Avoid using URLs for sessions IDs and make sure that the URL in use is terminated after logout
- Block the use of default credentials
- Limit the number of login attempts and monitor failed login attempts. Inform users and admins when an account is under cyber-attack
3. Sensitive Data Exposure

The data or information transmitted through HTTP is not encrypted when it goes through multiple routers. All types of data transfer in a web server from device to user travel between many nodes like office router, home router, provider router, host provider server, data centre router, and many more.
If any of these nodes contain malware, known as “sniffer”, the data is read and transferred to the hacker, which provides access to all types of sensitive and confidential data going through the different routers.
This insecure cryptography in data transfer leads to the vulnerability of sensitive information like bank account details and user passwords.
This OWASP top ten security risk can be avoided by:
- Enforce a Transport Layer Security (TLS) to protect data transfer
- Encrypt the stored data
- Implement HTTP Strict Transport Security (HSTS) for encryption
- User responses with sensitive data should not be saved in the cache
- Implement controls on different data classifications like stored, transmitted or processed
- Use robust and secure keys, protocols and algorithms
- Implement hashing functions like PBKDF2, Argon2, scrypt, brcrypt, etc.
4. XML External Entities (XXE)
XXE can be exploited in a wide variety of ways. It can be implemented in a complicated way or a simple way, if a part of external code reaches an XML document, then the web application has been breached and compromised.
The most famous XXE attack is called the “XML Bomb” or the “Billion Laughs” attack. This type of cyber-attack can overload the web application’s server and its resources quite simply. A hacker can define a tiny and insignificant element like “haha” or “lol” or a collection of other elements to shut down a specific server.
This OWASP top ten security risk can be avoided by:
- Train developers to test, recognize and deal with XXE attacks
- Implement simpler data formats like JSON to avoid serialization of sensitive data
- Implement whitelist server-side input authentication to avoid XML documents with malicious data
- Implement XSD validation to authenticate incoming XML using XML schema
- Ensure regular up-gradation and patching of XML libraries
- Manually review and analyse source code for anticipating XXE attack
5. Broken Access Control
This security risk in OWASP top 10 has resulted from the lack of authentication of accessibility when data or object is requested. Web applications implement permission checks before giving access to data on the user interface. However, if the data request is not carefully authenticated, hackers can trick the web application by using a falsified request to gain unauthorized administrative access to sensitive data and system functionalities without the required permissions. This can allow the hackers to add, tamper or delete important data for personal gain.
This OWASP top ten security risk can be avoided by:
- Provide access control through server-less API or trusted server-side code
- Avoid public resources
- Implement access control functions and use them all over the web application
- Implement record ownership
- Identify and track access control failures and let the admins and users know in case of suspicious login behaviour
- Unauthorize JSON Web Tokens (JWT) after logout
- Ensure that the wen roots don’t contain backup files and metadata
- Introduce integration and access control unit tests
- Remove invalid and inactive user accounts
- Introduce multi-factor authentication during login
- Introduce Principle of Least Privilege (PoLP)
6. Security Misconfiguration

The security of web applications controls the whole infrastructure, framework and all types of servers. Server component default settings are, most often than not, insecure and open to potential data leakage.
A disabled cookie HTTP only setting can easily lead to theft of session cookies through JavaScript in an XSS attack (section 7), and this is caused by the default setting. If the cookie HTTP only setting is enabled, then the session cookie remains secure from malicious hackers. Such a significant and simple setting is overlooked in most web applications with personal accounts and payment gateways.
The database server default settings like Memcached and Redis are also some examples of Security Misconfigurations. This weakness or vulnerability leads to situations where private sessions and services get displayed on public IP, making it easy for hackers to access and tamper data using an XSS attack.
The web application must be regularly updated and optimized to avoid this kind of data leakage because vulnerabilities emerge every day in different components of a web application. Your app may be secure, nicely written and carefully examined, still weaknesses and data leakage may arise in the web or operating server at any time.
This OWASP top ten security risk can be avoided by:
- Use a secure and safe web application installation process
- Automate the process of deploying a secure web application environment
- Eliminate rarely used features and frameworks and deliver a minimal web application
- Segregate the tenants and components by implementing segmented web application architecture
- Examine, review and regularly update the configurations of updates, patches, security notes and cloud storage permissions
- Automate the process of monitoring and authenticating the efficiency of the secure web application environment
- Automate workflows to ameliorate security issues in real-time
7. Cross-Site Scripting (XSS)
Cross-Site Scripting or XSS is another type of authentication error. Like an SQL injection, a hacker can steal session cookies and sensitive data using HTML injection. This type of injection is executed on the user’s browser.
Most web applications are exposed to this kind of HTML injection attack. User information like CVC code, bank account information, debit or credit card details, etc. are vulnerable to hackers. Using malicious scripts, user sessions can be stolen and information can be altered or monitored in real-time by hackers.
This OWASP top ten security risk can be avoided by:
- Distinguish and segregate unauthorized data input from live browner content.
- Using frameworks that prevent XSS attack by default like Ruby on Rails and ReactJS
- Follow OWASP’s cheat sheet for XSS prevention and avoid suspicious HTTP data requests in HTML
- Prevent DOM-based XSS by implementing context-sensitive encoding
- Introduce Content Security Policy (CSP)
8. Insecure Deserialization
When using object-oriented programming frameworks like .Net or Java for building a web application, deserialization and serialization are crucial concepts.
A security breach or data leakage occurs when the web application exhibits insecure or vulnerable deserialization.
In default settings for deserialization, a web application loses all control over what data is serialized or deserialized. This leads to incoming serialized data from unauthorized sources without any authentication or precautions. Other security issues that can occur because of this vulnerability are SQL injection, Application denial of service, Path Traversal and Remote Code Execution.
This OWASP top ten security risk can be avoided by:
- Avoid serialized data from suspicious sources
- Implement serialization methods that allow primitive data types
- Analyse the integrity of serialized data by introducing digital signatures
- Identify unanticipated clauses by implementing strict type constraints while deserializing
- Monitor scenarios where deserialization failed or acted suspiciously
- Run deserialization code by isolating it in low privilege environments to block unverified actions
- Eliminate exchange of network connectivity from deserializing containers and server
9. Using Components with Known Vulnerabilities
On many occasions, developers utilise frameworks or special libraries provided by third parties to build web applications. Most of these libraries, components and frameworks are open-sourced, giving source code access to people all around the world.
Hackers can study the vulnerabilities and weaknesses of the web application components to exploit them for personal gain.
This exposes the web application to different kinds of cyber-attack, leading to server takeover and data leakage.
This OWASP top ten security risk can be avoided by:
- Use frameworks, components and libraries from official sources
- Avoid components and libraries that are not maintained or updated regularly
- Deploy patches to identify and eradicate problems with unpatched frameworks
- Eliminate useless features, components, documentation and files
- Keep an on the sources for vulnerabilities and weaknesses in the components and update server-side and client-side inventory and dependencies regularly
- Frequently monitor, update, modify and optimize configurations of the web application
10. Insufficient Logging & Monitoring
This issue of insufficient logging and monitoring is not just faced by the internet web application, but by the entire Information Technology sector.
The core of this security risk is the number of logs, countless logs are being generated by modern systems. That’s why log management is a widespread issue.
The magnitude of the logged data is too huge to keep track of manually.
This security risk, when linked with inefficient integration with incident response leads to cyber-attacks that can persist for a long time, transfer to other systems and retrieve, modify or delete sensitive data.
The average time to identify a security breach or data leakage is more than 200 days, mostly noticed by external entities instead of internal monitoring.
This OWASP top ten security risk can be avoided by:
- Spot malicious accounts and activity by logging adequate user context during login, server-side input authentication failures, and access control failures
- For high-value transactions, introduce audit trails with integrity controls to prevent attempts of data leakage
- Utilise log formats that are easily handled by log management solutions
- Implement an incident response and recovery plan to prevent and anticipate cyber-attacks efficiently
Now that we’ve discussed the OWASP top ten security risks, here are a few of the other vulnerabilities you may face while maintaining a web or mobile application…
Other NON-OWASP Vulnerabilities
- Compromised passwords from other websites
- Access via malicious insider’s credentials
- Malicious website scraping
- Malware and phishing
- Physical theft
- Attacks via physical equipment (ATMs, POS)
- RDP exploits
Final Thoughts
The above-mentioned list of web application vulnerabilities must be avoided to eliminate the risk of potential data leakage and cyber-attacks.
The OWASP top 10 list of security risks spreads the awareness of web safety for developers and companies. From security breaches to sensitive data leakage, OWASP top 10 provides a detailed explanation of the most dangerous security risks.
We have encapsulated the latest list of top web application security risks and their solutions in this blog, and we hope it will help you in developing secure mobile and web applications for your end-users.
If you require further assistance or need answers to any queries, feel free to contact us.
With 16+ years of hands-on experience, Communication Crafts is a top-tier web development company and mobile application development company dedicated to helping businesses grow and flourish.
Our expert dedicated developers let you get involved in the project with a completely transparent development process to deliver cost-effective and customer-centric web applications.
We understand that this is a complicated subject for many readers, that’s why we’ve included an FAQ section…
FAQS – OWASP Top 10
What does OWASP stand for?
OWASP is the acronym for “Open Web Application Security Project”
WHAT IS AN OWASP VULNERABILITY?
OWASP vulnerabilities are security problems or weaknesses published by the Open Web Application Security Project. These issues are gathered by businesses, organizations, and security experts, which are then ranked by the seriousness of the security risk they pose to web applications.
WHAT ARE THE TOP 10 OWASP VULNERABILITIES?
OWASP’s top ten list is edited, compiled and published every three to four years, highlighting the most noteworthy web app security vulnerabilities. Also, the list includes examples of the weaknesses, how they can be exploited for cybercrimes, and suggested methods that reduce or eliminate application vulnerability.
WHAT IS THE NUMBER 1 APPLICATION SECURITY RISK REPORTED BY OWASP?
Injection is the number 1 flaw reported by OWASP. Injection can send suspicious data through SQL or other paths such as LDAP, allowing the interpreter to access unauthorized data or execute commands not intended by the application.
HOW CAN OWASP TOP 10 VULNERABILITIES BE TESTED?
OWASP provides an in-depth testing guide that offers test cases for a series of test scenarios. Many web app security teams have adopted a more automated solution by utilizing software to scan code for vulnerabilities with automated warnings and consistent application of best practices.
HOW SHOULD THE OWASP TOP 10 BE USED?
OWASP’s top 10 list offers a tool for developers and security teams to evaluate development practices and provide thought related to website application security. It does not make your web application free of vulnerabilities, but it provides a benchmark that encourages visibility of security considerations and concerns.
 Blog Communication Crafts
Blog Communication Crafts